You are here
Usage Models
In the following text, the highest priority usage models identified by the SIG's marketing group are briefly introduced. Each usage model is accompanied by a Profile.
Profiles define the protocols and protocol features supporting a particular usage model. Bluetooth SIG has specified the profiles for these usage models. In addition to these profiles, there are four general profiles that are widely utilized by these usage model oriented profiles. These are the generic access profile (GAP), the serial port profile, the service discovery application profile (SDAP), and the generic object exchange profile (GOEP).
File Transfer
The file transfer usage model (See also the file transfer profile) offers the ability to transfer data objects from one device (e.g., PC, smart-phone, or PDA) to another. Object types include, but are not limited to, .xls, .ppt, .wav, .jpg, and .doc files, entire folders or directories or streaming media formats. Also, this usage model offers a possibility to browse the contents of the folders on a remote device.
In the following figure, the required protocol stack presented for this usage model is presented. The figure does not show the LMP, Baseband, and Radio layers although those are used underneath (See Figure 2).
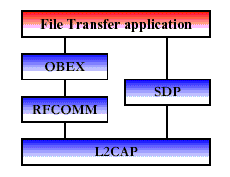
Fig 1: Protocol Stack for File Transfer Applications
Synchronization
The synchronization usage model provides a device-to-device (phone, PDA, computer, etc.) synchronization of the PIM (personal information management) information, typically phonebook, calendar, message, and note information. Synchronization requires business card, calendar and task information to be transferred and processed by computers, cellular phones and PDAs utilizing a common protocol and format. The protocol stack for this usage model is presented in Figure 4. In the figure, the synchronization application block represents either an IrMC client or an IrMC server software.
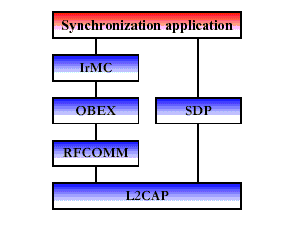 Fig 2: Protocol Stack for Synchronization
Fig 2: Protocol Stack for Synchronization
Three-in-One Phone
Telephone handsets built to this profile may connect to three different service providers. First, telephones may act as cordless phones connecting to the public switched telephone network (PSTN) at home or the office and incurring a fixed line charge. This scenario includes making calls via a voice base station, making direct calls between two terminals via the base station and accessing supplementary services provided by an external network. Second, telephones can connect directly to other telephones for the purpose of acting as a ~Swalkie-talkie~T or handset extension. Referred to as the intercom scenario , the connection incurs no additional charge. Third, the telephone may act as a cellular phone connecting to the cellular infrastructure and incurring cellular charges. The cordless and intercom scenarios use the same protocol stack, which is shown in Figure 5. The audio stream is directly connected to the Baseband protocol indicated by the L2CAP bypassing audio arrow.
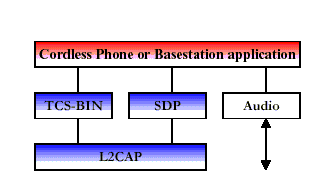
Fig 3:Protocol Stack for Cordless Phone and Intercom Scenarios
Ultimate Headset
The headset can be wirelessly connected for the purpose of acting as a remote device~Rs audio input and output interface. The headset increases the user~Rs freedom of movement while maintaining call privacy. A common example is a scenario where a headset is used with either a cellular handset, cordless handset, or personal computer for audio input and output. The protocol stack for this usage model is depicted in Figure 6. The audio stream is directly connected to the Baseband protocol indicated by the L2CAP bypassing audio arrow. The headset must be able to send AT-commands (Attention commands) and receive result codes. This ability allows the headset to answer incoming calls and then terminate them without physically manipulating the telephone handset.
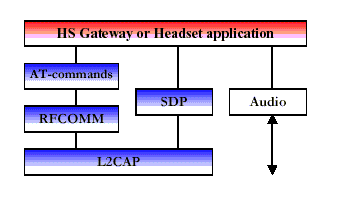
Fig 4: Ultimate Headset Protocol Stack
